Ten years ago, 12-year-old Rory Staunton dove for a ball in gym class and scraped his arm. He woke up the next day with a 104° F fever, so his parents took him to the pediatrician and eventually the emergency room. It was just the stomach flu, they were told. […]
Information and Communication Technology (ICT) is the means of processing data, with a focus on the use of communication devices, computers, and software programs to transform, store, secure, transfer, and recover information from any location and at any moment. The significance of ICT cannot be confined because of the […]
After more than a decade of innovation in the high-end headphone and IEM categories, it is interesting to take stock of the smaller brands that are still around and prospering. FiiO were part of the first wave of high-end Chinese portable audio products; the original FiiO X1 became one of […]
Aspiring polyglots can be stymied by differing keyboard layouts and character sets when switching between languages. [Thomas Pollak]’s Poly Keyboard circumvents this problem by putting a screen in every key of the keyboard. In his extensive build logs, [Pollak] details the different challenges he’s faced while bringing this amazing keyboard […]
Want an effective method to hack a Gmail account? A safe technique that can easily allow you to successfully hack? Let’s just say that is exactly the purpose of this article. However, our writings have an educational objective. This is not an incitement to hacking. You should know that hacking […]
This network mapping may also identify a particular strategy used by bad actors of splitting their edit histories between a number of accounts to evade detection. The editors put in the effort to build reputation and status within the Wikipedia community, mixing legitimate page edits with the more politically sensitive […]
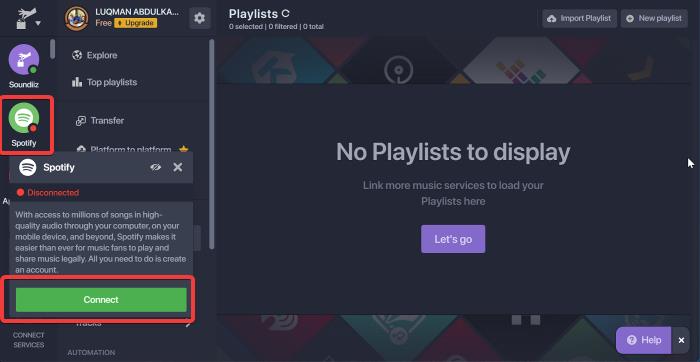
Spotify and Apple Music are at the forefront of the conversation when it comes to online music streaming services. Despite the fact that these two streaming platforms offer the best user experiences, there may be times when you need to transfer from one to the other. It’s quite easy to […]
NFT expert answers the world’s most Googled NFT questions, including revealing if they’re a better investment than cryptocurrency. “What is an NFT?” is searched an average of 948,000 times each month around the world The second most searched NFT question is “How do you create an NFT?”, which is Googled […]
Apple made the iPhone the center of your digital life, turning into a sort of media, email, health, and security hub. An Apple Watch is an even further distillation of truly personal technology. Apple relies on proximity and other cues to let a Watch, iPhone, and Mac unlock each other […]
When you mention Stax in headphone circles, everyone seemingly claims to either own a pair or have plans to buy one of their electrostatic headphones. The iconic loudspeaker brand changed hands in 2011 and has been owned by Edifier in China ever since. Edifier is better known for it affordable […]